Businesses still rely on inadequate controls for third-party cyber risk, but change is on the horizon


As 2023 unfolded with unprecedented incidents involving third-party services like MOVEit Transfer and GoAnywhere, it was clear to us at Tenchi Security that third-party cyber risk management (TPCRM) was more important than ever. So, when we organized our Tenchi Conference at the end of the year, we took the opportunity to conduct a survey and gather insights into how organizations were tackling this challenge.
Not only did we find that businesses sometimes have hundreds—if not thousands—of third parties, but many are also considered critical for their operations. Despite this, the cybersecurity posture of third parties is still being determined using questionnaires, industry certifications, or point-in-time scans that do not provide real-time discovery and visibility of cybersecurity risks.
Our survey shows that questionnaires are still employed by 90% of organizations, being the most common method of assessing a third party. Third-party audits and certifications (such as SOC2 and ISO 27001) come in second place, with an adoption rate of 68% (note that companies can and very often do employ more than one type of assessment).
Around 60% of organizations repeat these “static” assessments only once a year.
These numbers indicate that organizations still rely heavily on assessments confined to a specific time and need more proper visibility into the dynamics of day-to-day operations. Though questionnaires and certifications may have a role in determining whether or not an organization has some understanding of cybersecurity best practices and policy, they need more insight into the tangible implementation of that understanding.
To illustrate, it’s akin to contracting a third party for manufacturing and never checking if the products they deliver over time are as safe as the prototype they showed when the deal was initially closed. It might seem obvious that this isn’t a good idea, but cybersecurity is often less intuitive than physical risks.
Thus, many organizations have an opportunity to improve their third-party risk assessment programs by adopting faster and more seamless assessment strategies.
At Tenchi, we believe the right way to approach this challenge is through continuous inside-out monitoring, which leverages the business’s relationship with third parties to provide accurate and constantly updated assessments of their security posture. Organizations should also go beyond admiring the problem and work cooperatively with third parties to ensure risks are identified and mitigated over time.
Why this matters
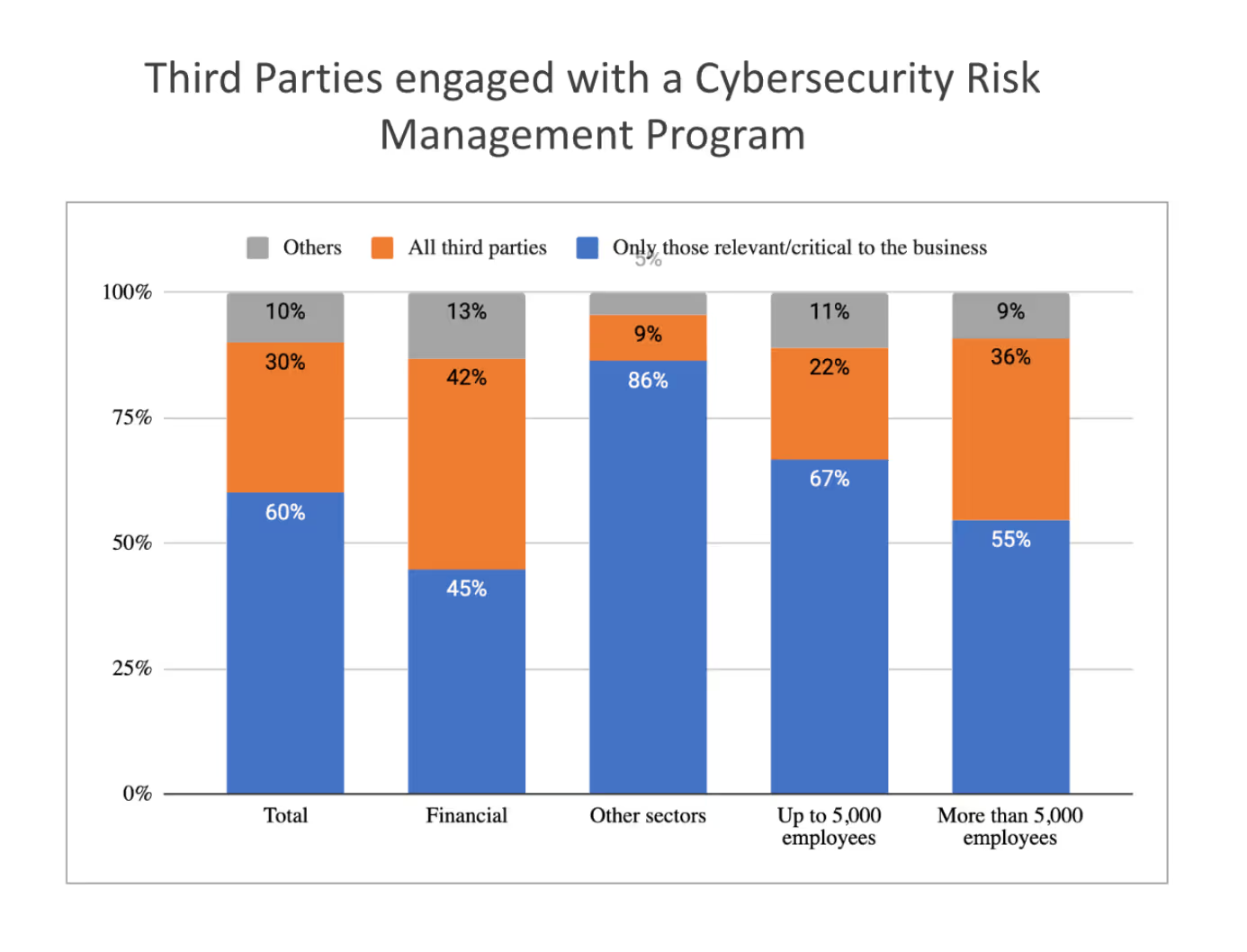
At the end of 2023, a Gartner survey found that 45% of organizations had suffered business interruptions related to third parties in the two years prior. More recently, Verizon’s Data Breach Investigations Report (DBIR) told a similar story (as we covered), with third-party incidents like MOVEit Transfer showing they can single-handedly change the landscape for sectors like education or finance.According to our survey, half of the companies with 501 to 1,000 employees contracted at least 100 third parties. For larger organizations with over 5,000 employees, 30% have over 3,000 vendors and partners, and 79% rely on over a thousand third parties. That is an extensive attack surface; only some of these third parties are monitored or managed. In general, only third parties that are relevant and critical to the business are included in a third-party risk management program.
It’s little wonder that threat actors have embraced the strategy of looking into vendors to carve a path toward their actual targets. In 2021, many businesses were affected when a ransomware group exploited a vulnerability in software from Kaseya to hit managed service providers and, in turn, their customers. More recently, healthcare providers in the United States had to deal with the fallout from a breach at Changed Healthcare, which delayed payments and left systems unavailable.
This approach has been observed in more targeted incidents, too. Attackers hit identity services, email providers, and even marketing agencies or law firms that were hired by their targets.
(If you want to keep up with the latest third-party incidents, check out Alice in Supply Chains, our monthly ad-free newsletter. You can subscribe from our home page or LinkedIn.)
This type of supply chain exploitation was recently highlighted by a White House report, which explains that “adversaries are increasingly taking advantage of complex and interconnected relationships between organizations and their suppliers, customers, vendors, and service providers, compromising single nodes that grant surreptitious access to victims in the United States and around the world.”
Since this issue has drawn the attention of lawmakers, it’s safe to say some organizations will soon have to adapt to regulations aimed at taking on this third-party risk.
But even those who won’t be covered by these new rules have much to gain from being proactive and making sure that their third-party risk management programs are up to the task of defending the organization from these emerging threats — to protect their data from ransomware and avoid downtime, and develop stronger relationships with their partners for a competitive edge.
An ongoing effort – for everyone
Our survey found that some businesses still lack a proper third-party cyber risk management (TPCRM) program. 14% of our respondents said their organizations do not have one. Even among companies with over 5,000 employees, this figure is still 11%.
The numbers are even more worrisome when we look outside the financial sector. When excluding this group, 24% of participants answered that their organizations lacked a TPCRM program.
Today, organizations reliance on third parties is only growing. Unfortunately, this reduces their visibility over the problem, so there’s little reason to ask how many third parties they have. They likely wouldn’t know.
However, all the participants who answered they don’t have a TPCRM program also said they want to build one, with 40% indicating they would like to have it in place within a year.
We also found that 70% of businesses managing third-party cyber risk have only started their program in the last five years. Many (38%) started less than two years ago. This means everyone can still learn and improve a lot—on both sides of this relationship.

Methodology and survey data
This survey’s answers were collected in person from 70 attendees of our Tenchi Conference in November 2023. All participants are professionals or executives in cybersecurity, risk management, data privacy, or procurement.
As the Tenchi Conference took place in São Paulo, the survey focuses on the Brazilian landscape, even though many of the companies present are multinationals. Large organizations in the financial sector are also highly represented in the data set.
The breakdown is as follows:
- 51% are in the financial sector, and 10% operate in telecommunications. The remainder is spread between consulting and professional services, healthcare, technology, retail, and law.
- 65% of respondents work in organizations with over 1,000 employees, with 41% saying their organizations employ over 10,000 people. 12% are smaller businesses with 50 or fewer employees.


