Google Workspace Administrator 2FA Enforcement Issues


Blog Update: July – 15th – 2024:
We’d like to give you an update on the OU-level MFA enforcement issue identified in this blog. As of July 12th, 2024, Google’s engineering team indicated they had remedied the issue. However, please do your due diligence to validate and confirm that your Google Workspace MFA enforcement policy operates as expected.
If your Google Workspace account has gone through Google’s MFA enforcement for admins and you are using OU-level MFA enforcement, your MFA enforcement may not work.
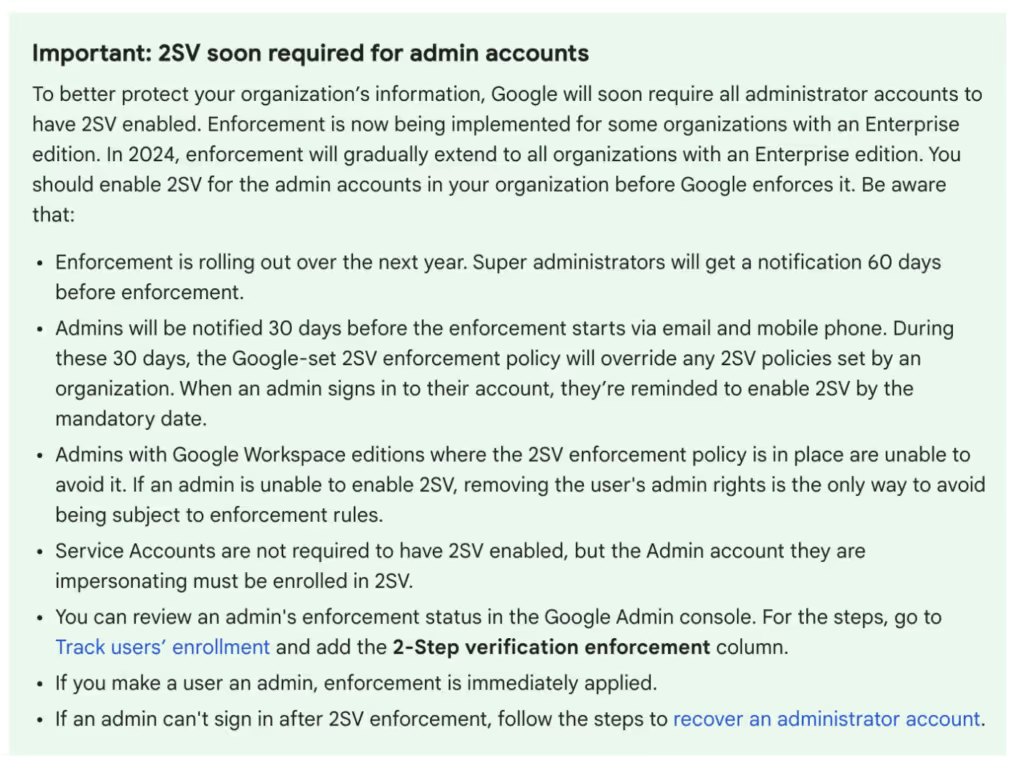
Google, following Github in an epic effort to improve the security of its users, recently made it public that all Google Workspace administrators will have MFA (Multi-factor authentication) enforced. The Google MFA policy will be a gradual rollout, and in our case, the change was implemented and enforced starting July 3rd.
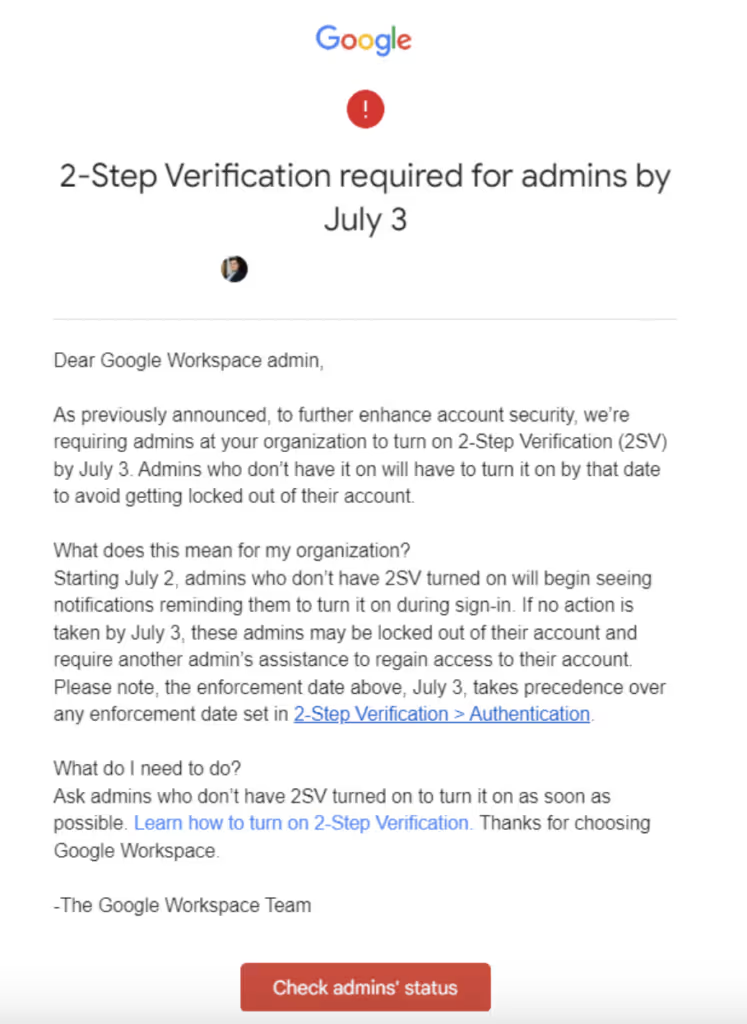
We already had an OU-level policy enforcing MFA for all users, including administrators. Therefore, when we received the email stating that MFA would be enforced on July 3rd, we expected no actions to make changes would be necessary. However, on July 3rd, it became clear to our security team that our MFA implementation had changed because we identified that our MFA policies were affected in our environment.
At Tenchi Security, we eat our own cooking. In other words, we secure our security by using our product, Zanshin, to scan ourselves and be transparent to all our customers about our security controls. This includes cloud providers (IaaS, PaaS, and SaaS). The big surprise was that our product alerted us last Thursday (July 4th, 2024) that we needed to have MFA enforced on our Google Workspace administrators.
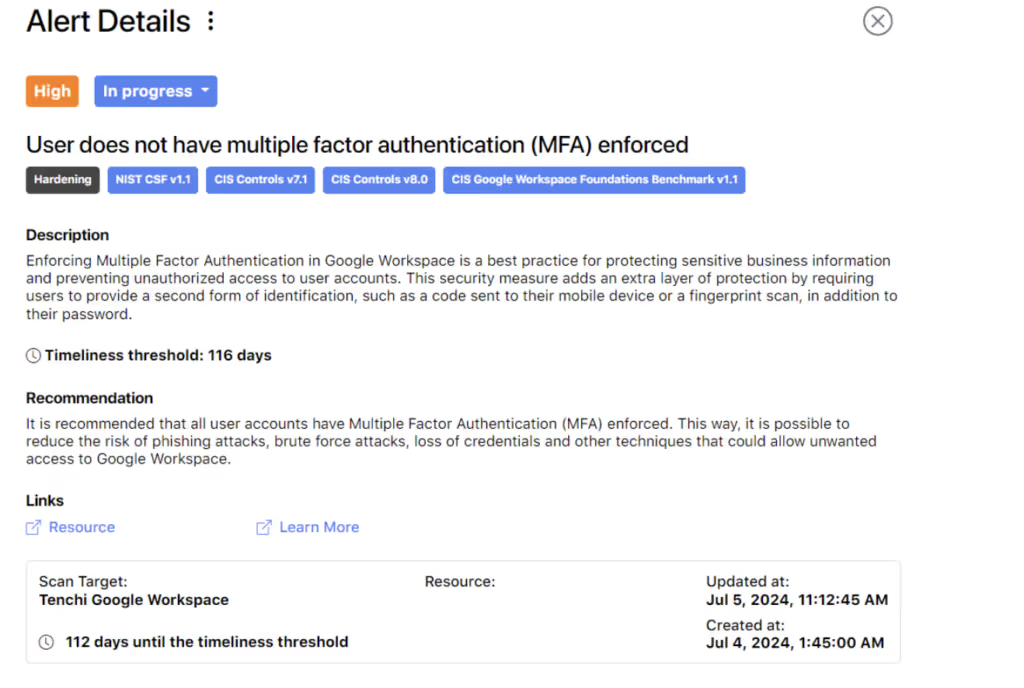
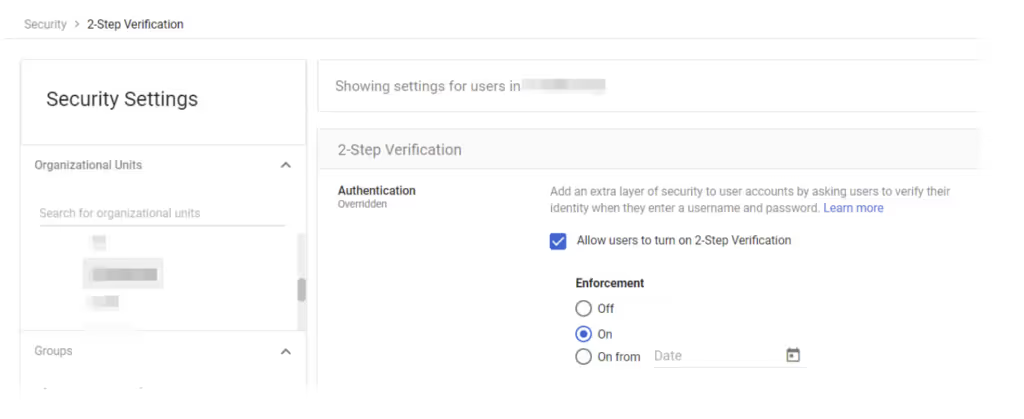
When analyzing the alert, we verified that the OU to which this user belonged did enforce MFA:
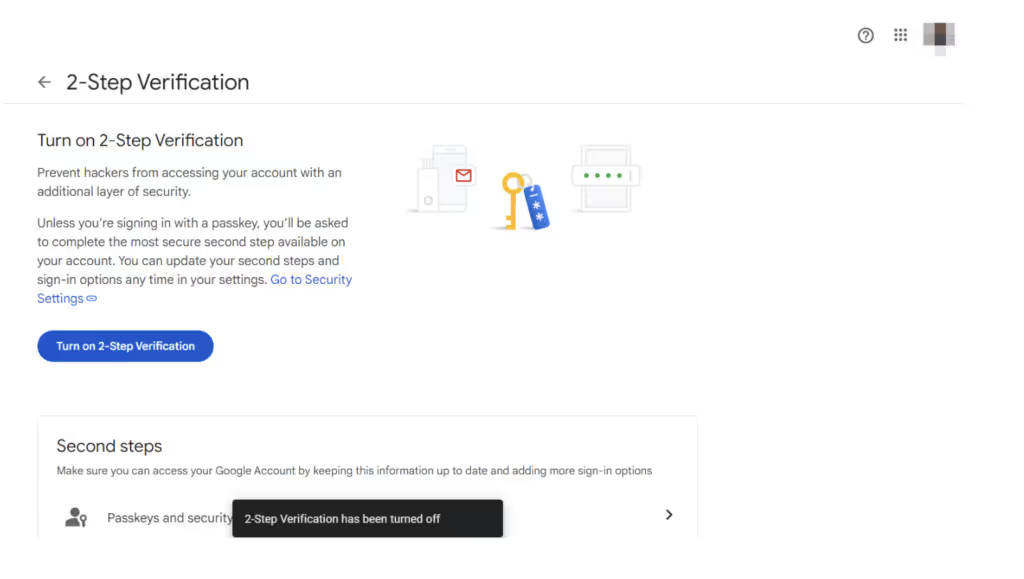
However, and this is the problematic part when accessing an admin user’s profile, Google Workspace indicates that MFA verification is not enforced for this user:
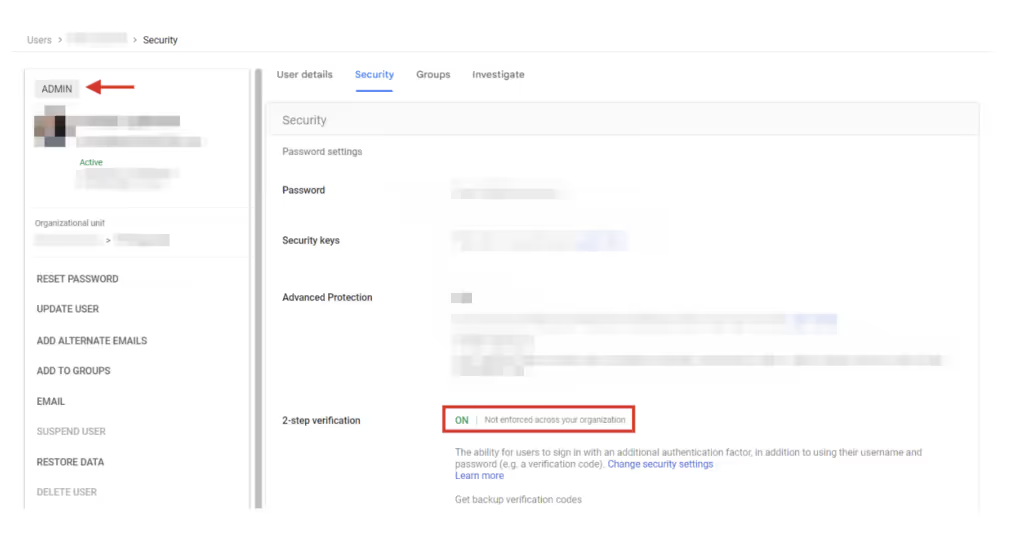
We then confirmed that the 2-step verification setting can be disabled for this user in their user profile settings, even when the OU-level setting says they should not be able to.

After confirming the issue in our environment, we contacted Google’s support team. We explained the issue to them and shared our evidence. They executed internal tests and confirmed the issue. They also informed us that the issue had been escalated to the engineering team.
Timeline:
- July 3rd, 2024 – Google implemented the change in our organization
- July 4th, 2024 – Zanshin starts alerting on the lack of 2FA enforcement for admin accounts
- July 5th, 2024 – The Tenchi Security team investigates the issue
- July 5th, 2024 – The Tenchi Security team contacts the Google Support team by email
- July 12th, 2024 – The Google team has fixed the issue
The Google team fixed the issue on July 12th, 2024. However, we recommend you perform regular checks to ensure all your admin accounts have an organization-approved 2FA enabled.
We are not aware of any possible mitigations other than increased monitoring. If your organization was similarly impacted, we recommend you perform regular checks to ensure all your admin accounts have an organization-approved 2FA enabled until Google resolves this issue.
We’re thrilled that our product has been, as far as we know, among the first (if not the first) to detect this issue. Monitoring your and your third party’s environment for issues is crucial across highly connected supply chains. Although not a critical security issue, this event shows the value of data-driven, evidence-based monitoring in detecting and directly mitigating risk.
References:
https://www.linkedin.com/posts/sieira_2fa-saas-security-activity-7216144640066932736-46vN
https://support.google.com/a/answer/175197#2SV
Note: This blog post was updated to reflect the fix implemented by the Google Team on July 12th, 2024.


