Detecting abuse in the AWS control plane in an actionable wayusing Det{R}ails


When questioned about how to properly monitor AWS environments, especially the control plane, the answer will certainly involve the use of CloudTrail logs. To clarify, when we mention the “control plane”, we are referring to the actions taken using the AWS API, such as: creating an IAM user, increasing a privilege, starting an instance, giving access to a database, allowing access to a network port among hundreds of other possible options.
What characterizes CloudTrail logs as a data source is its granularity, consisting of events structured in JSON objects with several complex and nested fields. Those are necessary to represent all the extra information for an event to be more actionable. After all, the AWS control plane has more than 7,400 actions, divided among more than 200 services. Each of these actions is roughly equivalent to AWS API calls, and each one of these actions involves different parameters with greatly varied data types.
Access Control to the control plane involves authentication via user and password (for the Web Management Console) or an access key ID and secret access key to use tools based on the SDKs or the AWS CLI. There are several ways to gain access to access credentials, some legitimate and others not so much. These are a few of them:
- Portal / API (at creation);
- Abuse of applications in the cloud;
- EC2 Instance Metadata Service;
- Code leaks;
- Endpoints used by teams with legitimate access (.aws / credentials);
- Third parties such as SaaS solutions, MSPs, or consultancies (Cross-Account Access);
- Tools Configuration (CI / CD, Scanners …).
Once an attacker gains access to a key, they can perform several attack techniques, such as:
- Enumeration (users, privileges, services)
- Escalation of privileges
- Lateral movement
- Exploration
- Persistence
- Exfiltration
- Evasion
Organizations should use CloudTrail log monitoring to detect and react to this kind of malicious activity quickly. This will require a good understanding of what normal activities look like in the environment, as well as the judicious use of correlation rules and enrichment of events to allow more effective and efficient detection and investigation. In order to help organizations put this into practice, we created Det{R}ails, presented in its initial version today at the SecTor Conference (Canada).
The Det{R}ails Project (CloudTrail in Details) is being developed by the research team at Tenchi Security to improve how organizations can leverage CloudTrail events. It is built on top of ElasticStack, the current version of the project introduces an interesting set of enrichments that can be summarized as follows:
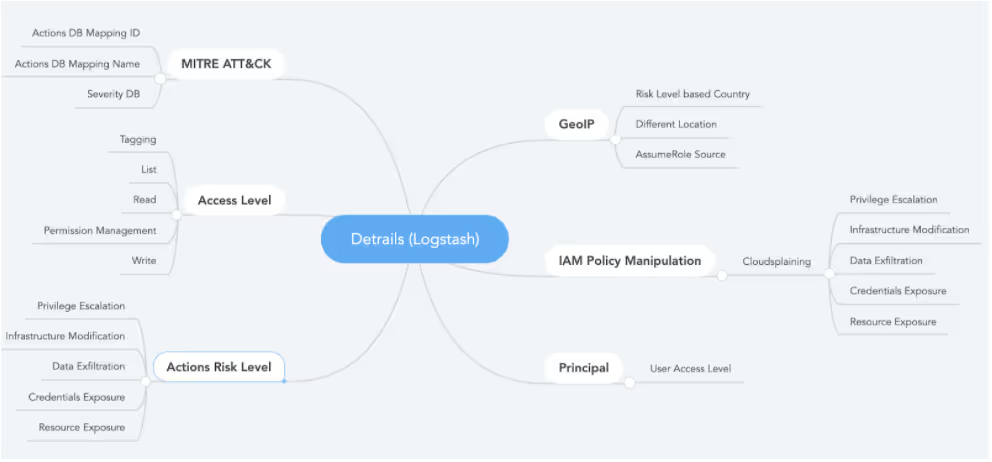
An interesting source of inspiration and enrichment data was the fantastic open-source tool CloudSplaining (created by Kinnaird McQuade of Salesforce). It was designed to analyze the environment on demand, but we adapted it to run as IAM policy creation or changes are reported to have occurred on CloudTrail events.
Other interesting enrichments that we must mention:
- AssumeRole origin for later verification if the key is being used from a different source
- Action Access Level (based on AWS documentation)
- MITRE ATT&CK (when the action is related to a technique)
- Risk Level, also based on CloudSplaining but applied to each action separately, adding information about the type of damage the action can cause: Elevation of Privileges, Exposure of Resources, Data leakage, Leakage of credentials and affected services.
All these enrichments were implemented in Logstash, before events are sent to Elasticsearch, according to the usual ElasticStack architecture. An interesting benefit of this is that enriched events could be sent from Logstash to any other SIEM or big data solution if necessary, given how flexible it is., This will easily allow for integration with pre-existing event management infrastructure.
The screenshots below showcase some of the dashboards we built from actual data with these enrichments:
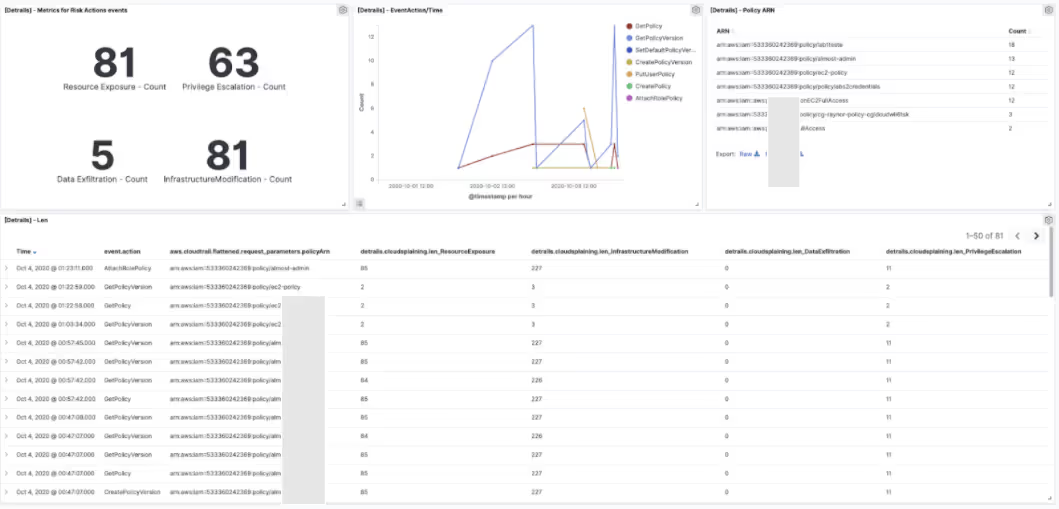
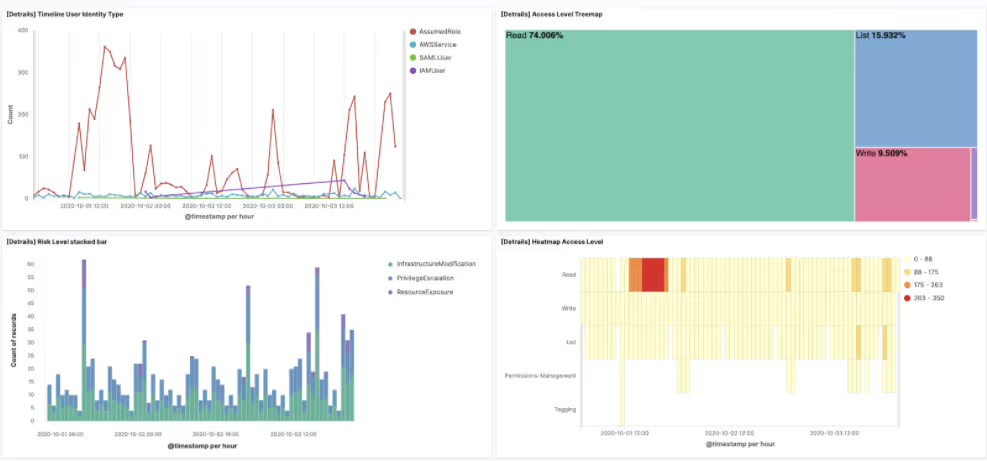
To demonstrate the usefulness of this approach, we performed simulations of two scenarios in which we applied some detection engineering: elevation of privileges and use of the PACU Framework.


To access the slides, click here: https://www.slideshare.net/tenchisecurity/detecting-aws-control-plane-abuse-in-an-actionable-way-using-detrails. The video is available at https://sector.ca/sessions/detecting-aws-control-plane-abuse-in-an-actionable-way-using-detrails/.
Don’t hesitate to get in touch if you want to learn more about how Tenchi Security can help your organization optimize its cloud security monitoring and incident response practices.
Happy Detection!
Written by Rodrigo Montoro, Felipe Espósito and Alexandre Sieira.


